How can you keep sensitive information in your Django app safe and hidden?
Every Django app needs to handle environment variables securely. This keeps sensitive data safe and helps maintain app integrity. Environment variables are a secure way to store sensitive data. They keep things like database passwords, API keys, and secret tokens hidden from your codebase. This guide shows how to secure environment variables in Django. It offers best practices and uses the python-decouple and python-dotenv tools.
Why Use Environment Variables in Django?
Storing API keys, database credentials, and SECRET_KEY, alongside settings.py in Django, represents a significant security vulnerability. Data access and security breaches become possible when someone finds this sensitive information in open-source repositories or code-sharing platforms.
Environment variables help secure secrets because they store the data outside your project code. This technique helps protect data better, making environment setups easier and deployment simpler across different operational zones.
Key benefits include:
- Improved Security: The version control system, like GitHub, doesn’t save sensitive data. This cuts down its risk of exposure.
- Environment-Specific Settings: Managing different operating setups across development, staging, and production environments is easier.
- Simplified Deployment: Due to this method, the secure deployment of applications becomes possible through multiple environments.
- Reduced Human Error: Django negates the potential mistakes that develop when staff change configurations manually.
- Easier Collaboration: Programming code sharing becomes possible without permitting developers to share their critical credentials.
Understanding Environment Variables in Django
External values called environment variables give your application the needed configuration data. In Django applications, you keep vital information inside environment variables such as SECRET_KEY, DATABASE_URL and EMAIL_BACKEND.
- SECRET_KEY: Django uses this key to protect its sessions and cookies with 7encryption.
- DEBUG: The system lets you change from development mode to regular operation by setting a simple on/off setting.
- DATABASE_URL: Connection string for your database (PostgreSQL, MySQL, etc.).
- EMAIL_BACKEND: Email provider configuration for sending application emails.
Storing variables in the environment keeps them secure since they stay separate from your source code.
Setting Up Environment Variables in Django
To handle environment variables securely in Django, developers must set up their projects to pull secrets from outside sources. The two main ways to manage a Django environment are python-decouple and python-dotenv. Environment variables help keep your application secrets apart from the code. They offer two methods for doing this: improving efficiency.
1. Using python-decouple for Environment Management
Django projects manage environment variables using a popular library called python-decouple. The settings are separate from your codebase. This feature keeps sensitive information safe.
Step 1: Install python-decouple
pip install python-decoupleStep 2: Create a .env File
Create a new .env file in the root directory of your Django project. This file will store sensitive data.
SECRET_KEY=your-secret-key
DEBUG=False
DATABASE_URL=postgres://user:password@localhost:5432/dbnameAdd .env to your .gitignore file. This keeps sensitive information safe from version control systems.
Step 3: Configure settings.py
Next, update your settings.py file to use python-decouple for loading environment variables.
From decouple import config
SECRET_KEY = config('SECRET_KEY')
DEBUG = config('DEBUG', default=False, cast=bool)
DATABASE_URL = config('DATABASE_URL')2. Using python-dotenv (an alternative approach)
Python-dotenv is a tool for managing variables. It reads the values from .env files.
Step 1: Install python-dotenv
pip install python-dotenvStep 2: Update settings.py
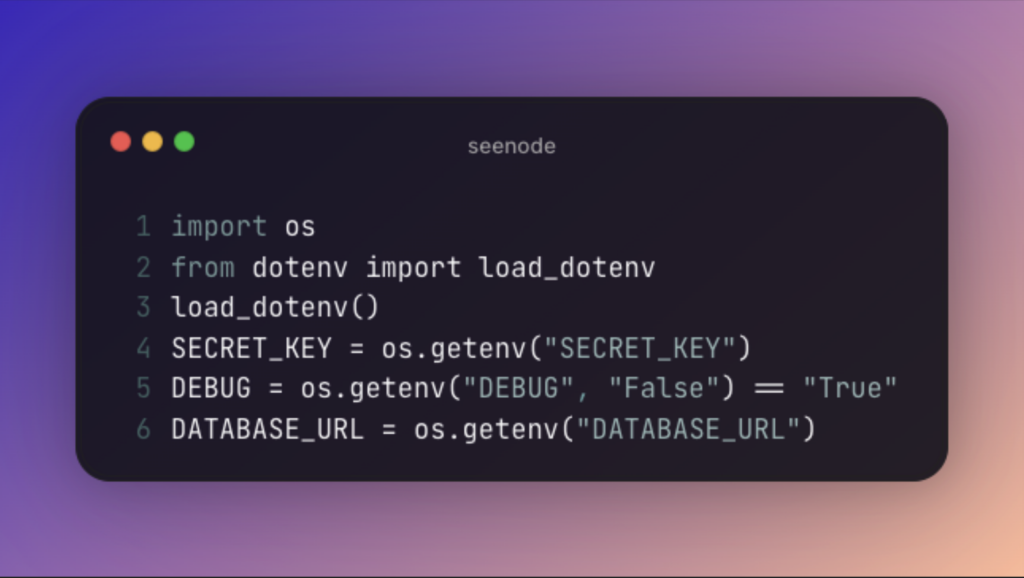
import os
from dotenv import load_dotenv
load_dotenv()
SECRET_KEY = os.getenv("SECRET_KEY")
DEBUG = os.getenv("DEBUG", "False") == "True"
DATABASE_URL = os.getenv("DATABASE_URL")3. Secure Environment Variables in Deployment
Deploying a Django application requires adding environment variables to your hosting platform’s secure secret management system. This ensures safe management during deployment. For example:
- Docker: Docker secrets should be used to handle critical data.
- Heroku: Deploy sensitive variables by accessing them via the dashboard and CLI interface.
seenode: The seenode environment protection system helps deputies safely store and retrieve deployment secrets.
Best Practices for Managing Environment Variables
Set these security steps to protect your Django project.
1. Avoid Hardcoding Secrets
Keep sensitive info out of your code files. This includes SECRET_KEY and API keys. Keep environment variable data stored outside your codebase.
2. Use .env Files for Development
Development teams should secure sensitive data by using .env files during development. Keep .gitignore safe during regular updates.
3. Manage Secrets Securely in Production
When putting .env files in production mode, you need other security measures.
Use secure methods for managing data, like:
- AWS Secrets Manager
- Azure Key Vault
- Kubernetes Secrets
- Seenode’s Secure Environment Management
4. Limit Access to Sensitive Data
Only employees or systems assigned to this task can access environment variables.
5. Rotate Secrets Regularly
Change sensitive credentials regularly. This helps keep your systems safe from long-term risks.
6. Audit Environment Variables
Regularly check your app’s environment variables. Look for any unused settings to remove.
7. Use Encryption for Sensitive Data
Store confidential data in encrypted files when your hosting environment allows it. This adds extra security.
8. Secure CI/CD Pipelines
Check that your CI/CD system can protect secret data during production. Apply protected storage for sensitive data while limiting variable viewability at build time.
9. Use Environment-Specific Files
When you deploy your app to different environments, use separate .env files. This helps manage settings for each platform. This prevents errors by matching proper variables with the appropriate stage of development.
10. Implement Monitoring and Alerts
Create monitoring tools that notice when environmental values change. These checks help maintain system integrity. They catch anyone who makes unauthorized changes.
Secure Environment Variables with seenode
Seenode allows you to deploy cloud applications quickly and solve environment variable protection issues. With seenode, you can:
- Centralized Secret Management: Put every environmental setting within a secure storage area.
- Automate Secure Deployments: Your Django application needs to receive secure secret values at every deployment phase.
- Isolate Environments: You can easily divide your work environment values into development, staging and production setups.
How to Use seenode for Environment Variables:
- Access the Dashboard: Open the seenode project dashboard page.
- Add Environment Variables: Arrange all your protected data securely through the Environment Management Panel.
- Deploy Securely: Keep all secret data encrypted and separated from the central deployment system.
Seenode provides a reliable platform to manage and scale sensitive configurations throughout your Django application system.
Example Deployment Workflow
These are the steps to manage environment settings when deploying Django projects on seenode securely:
- Prepare Your Project: Use python-decouple or python-dotenv to load all secret data safely.
- Configure seenode: Set up needed secret values using the seenode dashboard features.
- Deploy: Move your project into service without exposing secret environment values.
Conclusion
Securing .env data in Django applications serves to guard privacy and supports a reliable programming architecture. Combining libraries python-decouple and python-dotenv with seenode security tools builds stronger and faster Django applications.