Deploying a Django project can be challenging, especially for developers who are new to production environments. Many issues arise due to misconfigurations, security oversights, or inefficient deployment practices. These mistakes when deploying django can lead to performance bottlenecks, security vulnerabilities, and unnecessary downtime, which can be costly for businesses and frustrating for users.
Understanding and avoiding these pitfalls is crucial for a smooth and efficient deployment process. Whether you’re working on a personal project, a startup, or an enterprise-level application, following best practices can save you time, reduce debugging efforts, and enhance the reliability of your application.
One common issue is leaving Django’s DEBUG mode enabled in production, which exposes sensitive information to potential attackers. Another frequent mistake is not properly configuring the database, leading to slow queries and potential data loss. Additionally, many developers overlook the importance of serving static and media files efficiently, often relying on Django’s built-in development server rather than using a dedicated web server like Nginx or a CDN.
Security is another major concern. Hardcoding secrets, failing to set up security headers, and neglecting logging and monitoring can leave your application vulnerable to attacks. A well-structured deployment strategy, including CI/CD pipelines and proper error handling, can significantly improve your application’s resilience.
In this guide, we’ll explore ten of the most common mistakes developers make when deploying Django projects and provide solutions to avoid them. By following these best practices, you’ll be able to deploy robust, secure, and scalable Django applications with confidence. Let’s dive in!
1. Using Django’s Default SECRET_KEY
Many developers mistakenly leave Django’s default SECRET_KEY unchanged or expose it in their version control. This can lead to security risks, including predictable cryptographic signing and potential breaches.
Mistake:
Keeping the default SECRET_KEY or exposing it in version control.
Solution:
Generate a unique, strong SECRET_KEY for production and store it securely in environment variables or a secrets manager.
import secrets
import secrets print(secrets.token_urlsafe(50))Use tools like django-environ to manage secrets securely.
2. Debug Mode Left Enabled in Production
Django’s debug mode is useful for development but should never be enabled in production. It exposes detailed error messages that can provide attackers with valuable information about your system.
Mistake:
Leaving DEBUG = True exposes sensitive error messages and internal data.
Solution:
Always set DEBUG = False in production and ensure proper logging is configured.
DEBUG = False
DEBUG = False ALLOWED_HOSTS = ['yourdomain.com']3. Serving Static and Media Files Improperly
A common mistake is relying on Django’s built-in development server for serving static and media files. This is inefficient and can lead to performance issues.
Mistake:
Using Django’s built-in development server for serving static files.
Solution:
Use a CDN or a web server like Nginx to handle static and media files efficiently.
For Nginx:
location /static/ {
root /path/to/static;
}
location /media/ {
root /path/to/media;
}Use django-storages for cloud storage solutions like AWS S3.
4. Missing Proper Database Configuration
Poor database configuration can lead to performance bottlenecks, inefficient queries, and even downtime if the database is not properly optimized.
Mistake:
Using SQLite in production or failing to optimize database connections.
Solution:
Use PostgreSQL or MySQL for better performance and reliability. Set connection pooling properly:
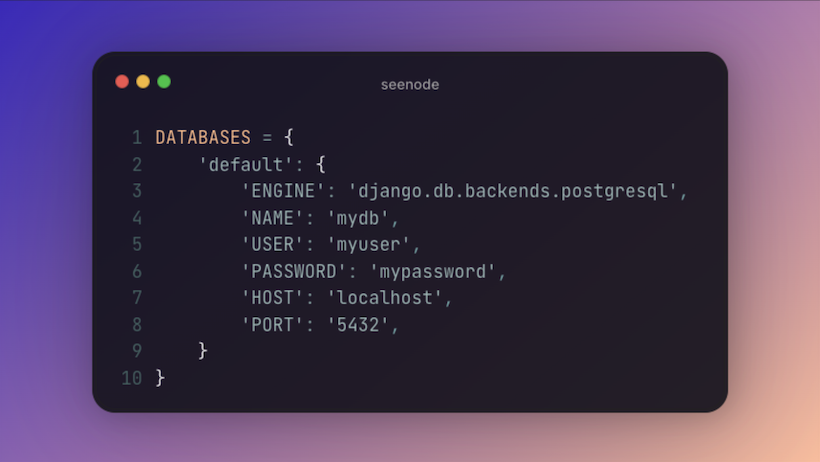
DATABASES = {
'default': {
'ENGINE': 'django.db.backends.postgresql',
'NAME': 'mydb',
'USER': 'myuser',
'PASSWORD': 'mypassword',
'HOST': 'localhost',
'PORT': '5432',
}
}Use pgbouncer for PostgreSQL connection pooling.
5. Not Using Environment Variables for Configuration
Hardcoding sensitive data like API keys and database credentials in settings.py is a serious security risk.
Mistake:
Hardcoding sensitive credentials in settings.py.
Solution:
Use environment variables or a configuration management tool.
import os
SECRET_KEY = os.getenv('DJANGO_SECRET_KEY')Use django-environ for easier management.
6. Poor Caching Strategy
Many developers overlook the importance of caching, leading to slow database queries and inefficient API calls.
Mistake:
Not using caching for expensive database queries or API calls.
Solution:
Use Redis or Memcached for caching.
CACHES = {
'default': {
'BACKEND': 'django.core.cache.backends.redis.RedisCache',
'LOCATION': 'redis://127.0.0.1:6379/1',
}
}Use @cache_page decorator for caching views.
7. Ignoring Security Headers
Failing to set proper security headers can leave your application vulnerable to common attacks like cross-site scripting (XSS) and clickjacking.
Mistake:
Not setting security-related HTTP headers.
Solution:
Use Django’s SecurityMiddleware and set strong security headers.
SECURE_BROWSER_XSS_FILTER = True
SECURE_CONTENT_TYPE_NOSNIFF = True
X_FRAME_OPTIONS = 'DENY'Use django-secure or django-csp for additional security.
8. Improper Logging and Monitoring
Without proper logging and monitoring, diagnosing production issues can become difficult, leading to increased downtime.
Mistake:
Not setting up proper logging and monitoring.
Solution:
Configure Django logging properly and use monitoring tools like Sentry or Prometheus.
LOGGING = {
'version': 1,
'disable_existing_loggers': False,
'handlers': {
'file': {
'level': 'ERROR',
'class': 'logging.FileHandler',
'filename': '/var/log/django_errors.log',
},
},
'root': {
'handlers': ['file'],
'level': 'ERROR',
},
}9. Lack of Proper Deployment Strategy
Manually deploying updates without automation can lead to inconsistencies, errors, and downtime.
name: Deploy Django
on: push
jobs:
deploy:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Deploy
run: ./deploy.shMistake:
Deploying updates manually without automation.
Solution:
Use CI/CD pipelines with GitHub Actions, GitLab CI, or Jenkins. Example GitHub Action for deployment:
10. Not Using a WSGI/ASGI Server
Using Django’s built-in runserver is not suitable for production as it lacks performance optimization and security features.
Mistake:
Running Django with runserver in production.
Solution:
Use Gunicorn (WSGI) or Daphne/Uvicorn (ASGI) for production servers.
For Gunicorn:
gunicorn
workers 3 myproject.wsgi:applicationFor ASGI with Uvicorn:
uvicorn myproject.asgi:application
host 0.0.0.0
port 8000Conclusion
Avoiding these common mistakes will improve the security, performance, and reliability of your Django deployment. Implement best practices such as proper configuration management, caching, logging, and automated deployments to ensure a smooth production experience.
Need help with your Django project deployment? Let us know.